Unlocking the Power of Google Chronicle SIEM
What is Google Chronicle SIEM?
Google Chronicle SIEM (Security Information and Event Management) is a powerful platform that allows organizations to monitor, detect, investigate, and respond to security threats in real-time. It provides a centralized view of an organization’s security posture, allowing for the proactive identification and mitigation of potential risks.
How does Google Chronicle SIEM work?
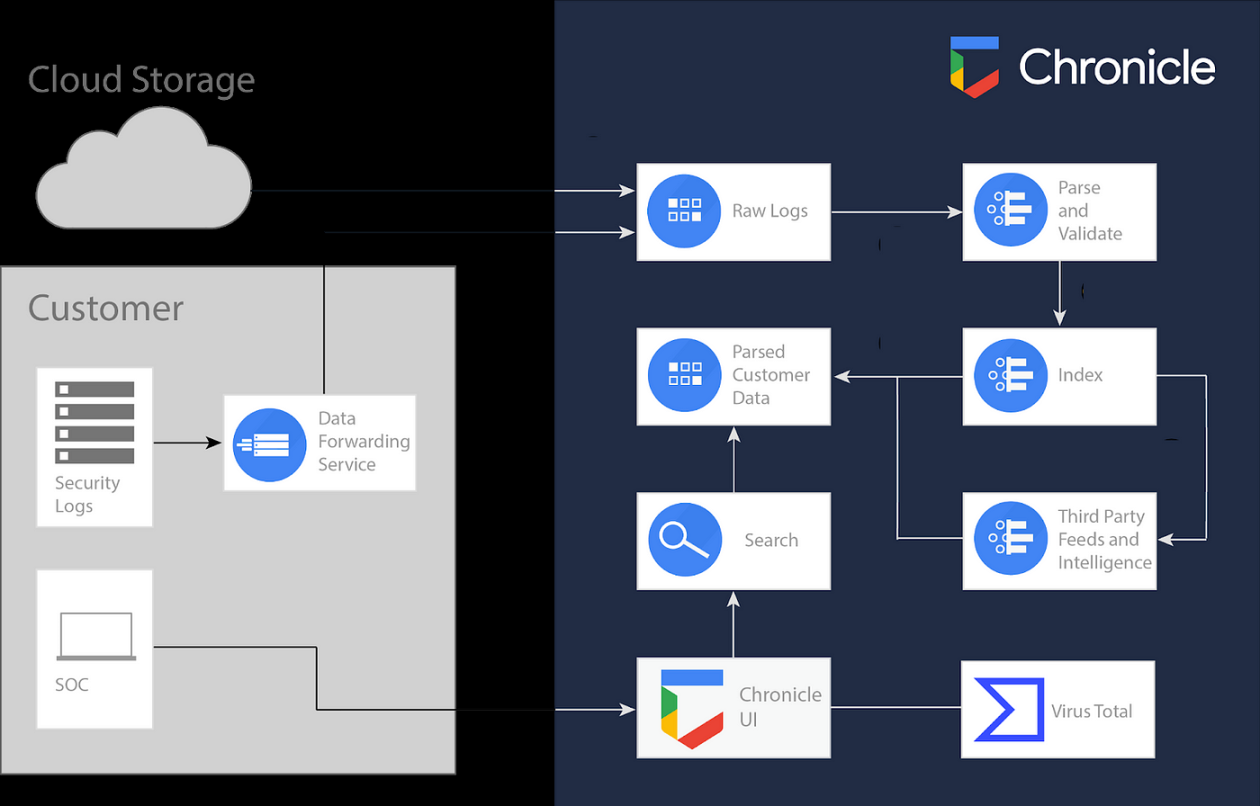
Google Chronicle SIEM works by collecting and analyzing data from various sources within an organization’s network, such as logs, events, and alerts. It uses advanced analytics and machine learning algorithms to detect anomalies and patterns that may indicate a security threat. The platform then provides detailed insights and recommendations for remediation, allowing security teams to respond quickly and effectively.
What is known about Google Chronicle SIEM?
Google Chronicle SIEM is known for its scalability, flexibility, and ease of use. It can handle large volumes of data from diverse sources, making it suitable for organizations of all sizes. The platform also offers customizable dashboards, reports, and alerts, allowing users to tailor the system to their specific security needs.
What is the solution offered by Google Chronicle SIEM?
The solution offered by Google Chronicle SIEM is a comprehensive approach to security monitoring and incident response. By providing real-time visibility into security events, organizations can proactively address threats before they escalate. The platform also offers automated response capabilities, reducing the time and effort required to mitigate security incidents.
Why choose Google Chronicle SIEM?
There are several reasons to choose Google Chronicle SIEM for your organization’s security needs. First and foremost, the platform is powered by Google’s advanced technology and expertise in cybersecurity, ensuring top-notch protection against evolving threats. Additionally, Google Chronicle SIEM is easy to deploy and integrate with existing security tools, making it a cost-effective solution for enhancing your security posture.
Our Experience with Google Chronicle SIEM
At our organization, we have implemented Google Chronicle SIEM to enhance our security monitoring capabilities. The platform has allowed us to gain a holistic view of our network security, enabling us to detect and respond to security incidents in real-time. With Google Chronicle SIEM, we have been able to streamline our incident response processes and improve overall security posture.
Conclusion
In conclusion, Google Chronicle SIEM is a powerful platform that offers advanced security monitoring and incident response capabilities. By leveraging Google’s expertise and technology, organizations can enhance their security posture and effectively mitigate security threats. With its scalability, flexibility, and ease of use, Google Chronicle SIEM is a valuable tool for any organization looking to strengthen their security defenses.
FAQs
1. Can Google Chronicle SIEM integrate with existing security tools?
Yes, Google Chronicle SIEM can integrate with a wide range of existing security tools, allowing for seamless deployment and enhanced security monitoring.
2. Is Google Chronicle SIEM suitable for organizations of all sizes?
Yes, Google Chronicle SIEM is scalable and can accommodate organizations of all sizes, from small businesses to large enterprises.
3. How does Google Chronicle SIEM help with incident response?
Google Chronicle SIEM provides real-time visibility into security events, allowing for quick detection and response to security incidents.
4. Can Google Chronicle SIEM automate security incident response?
Yes, Google Chronicle SIEM offers automated response capabilities, allowing for faster and more efficient mitigation of security incidents.
5. What sets Google Chronicle SIEM apart from other SIEM platforms?
Google Chronicle SIEM stands out for its advanced technology, scalability, and ease of use, making it a top choice for organizations looking to enhance their security defenses.