Understanding Cloud Security Controls
When it comes to protecting your data and ensuring the security of your online information, cloud security controls play a crucial role. In today’s digital age, with the increasing use of cloud services and storage, it is more important than ever to implement strong security measures to protect sensitive data from cyber threats. In this article, we will explore what cloud security controls are, how they work, what is known about them, and what solutions they offer for ensuring the safety of your data.
What Does It Mean?
Cloud security controls refer to the measures and protocols put in place to protect data stored in the cloud from unauthorized access, data breaches, and other cyber threats. These controls are designed to ensure the confidentiality, integrity, and availability of data in the cloud environment, helping to mitigate risks and prevent security incidents.
How Do Cloud Security Controls Work?
Cloud security controls work by implementing various security measures and technologies to protect data in the cloud. These measures may include encryption, access controls, authentication protocols, monitoring tools, and security policies. By implementing these controls, organizations can secure their data and prevent unauthorized access or data breaches.
What Is Known About Cloud Security Controls?
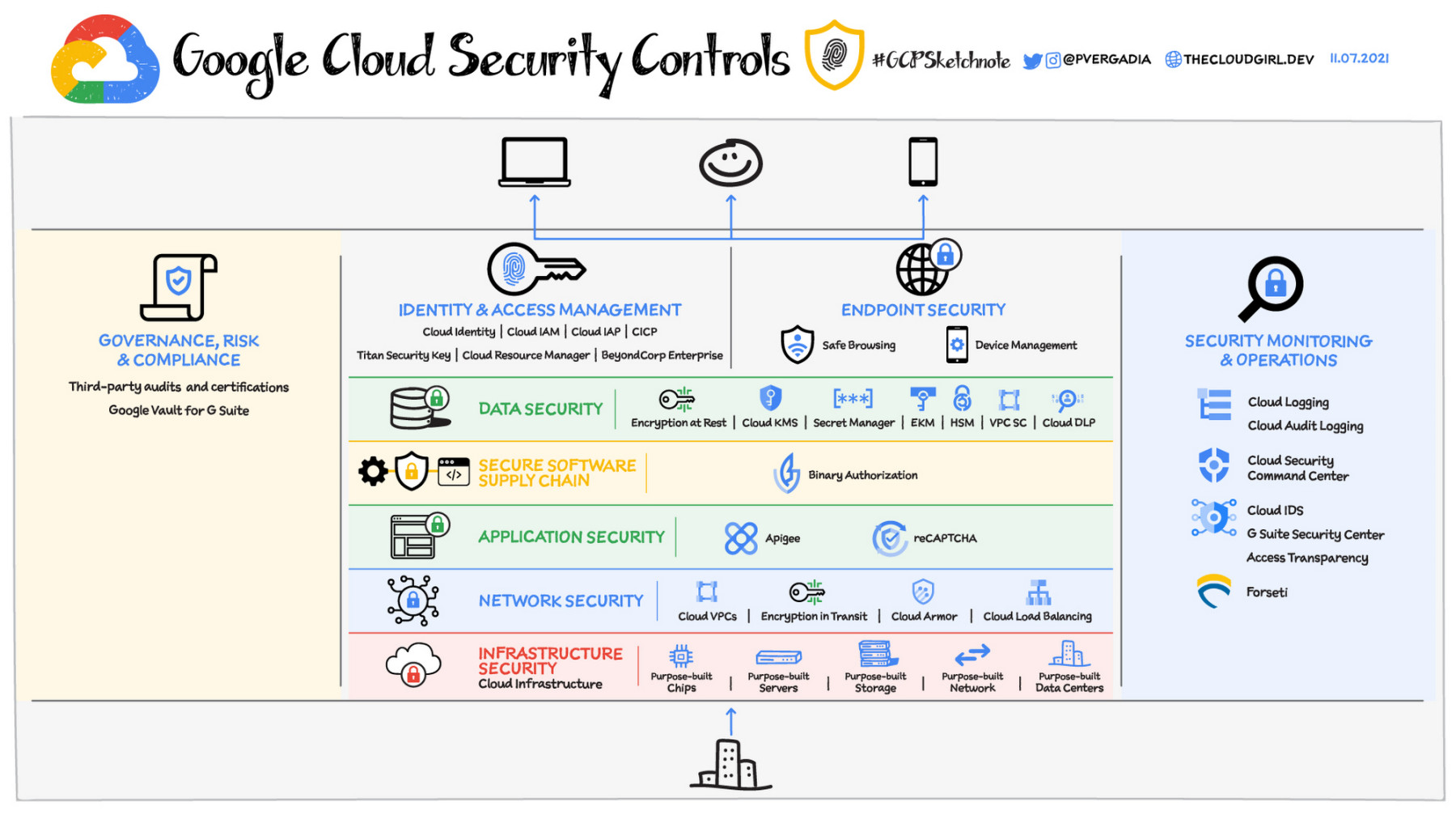
Cloud security controls are essential for ensuring the security of data stored in the cloud. They help organizations comply with regulatory requirements, protect sensitive information, and prevent cyber attacks. By implementing robust security controls, organizations can reduce the risk of data breaches and other security incidents, providing peace of mind for both businesses and their customers.
Solution Offered by Cloud Security Controls
Cloud security controls offer a solution for organizations looking to protect their data in the cloud. By implementing these controls, organizations can secure their data, prevent unauthorized access, and mitigate the risk of data breaches. These controls help organizations comply with security standards and regulations, ensuring the confidentiality and integrity of their data.
Information About Cloud Security Controls
Cloud security controls are essential for organizations that store data in the cloud. These controls help organizations protect their data, prevent security incidents, and ensure the confidentiality of sensitive information. By implementing robust security controls, organizations can maintain the trust of their customers and stakeholders, safeguarding their reputation and integrity.
Conclusion
In conclusion, cloud security controls are vital for ensuring the security of data stored in the cloud. By implementing strong security measures and protocols, organizations can protect their data from cyber threats, prevent unauthorized access, and comply with regulatory requirements. Cloud security controls offer a solution for organizations looking to secure their data and maintain the confidentiality and integrity of their information.
FAQs
1. What are some common cloud security controls?
Common cloud security controls include encryption, access controls, authentication protocols, monitoring tools, and security policies.
2. How do cloud security controls help prevent data breaches?
Cloud security controls help prevent data breaches by implementing strong security measures to protect data from unauthorized access and cyber threats.
3. Why are cloud security controls important?
Cloud security controls are important for ensuring the security of data stored in the cloud, protecting sensitive information, and complying with regulatory requirements.
4. How can organizations implement cloud security controls?
Organizations can implement cloud security controls by using security technologies, implementing security policies, and conducting regular security audits.
5. What are the benefits of using cloud security controls?
The benefits of using cloud security controls include protecting data from cyber threats, preventing data breaches, and maintaining the trust of customers and stakeholders.