Exploring the World of IBM Cloud Security
What is IBM Cloud Security?
IBM Cloud Security is a comprehensive set of tools, technologies, and practices designed to protect the data, applications, and infrastructure hosted on IBM Cloud. It encompasses a range of security solutions and services that help organizations secure their cloud environments and mitigate potential cyber threats.
How Does IBM Cloud Security Work?
IBM Cloud Security works by offering a multi-layered approach to security, incorporating various security controls and measures to protect cloud-based assets. These may include encryption, access control, threat detection, and incident response mechanisms, among others. By implementing these security measures, organizations can safeguard their sensitive data and ensure the integrity and availability of their cloud resources.
What is Known About IBM Cloud Security?
IBM Cloud Security is known for its robust security features and advanced threat intelligence capabilities. It leverages IBM’s expertise in cybersecurity and cloud computing to deliver cutting-edge security solutions that help organizations address their security challenges in the cloud. With IBM Cloud Security, organizations can benefit from a secure and compliant cloud environment that meets their specific security requirements.
Our Solution for IBM Cloud Security
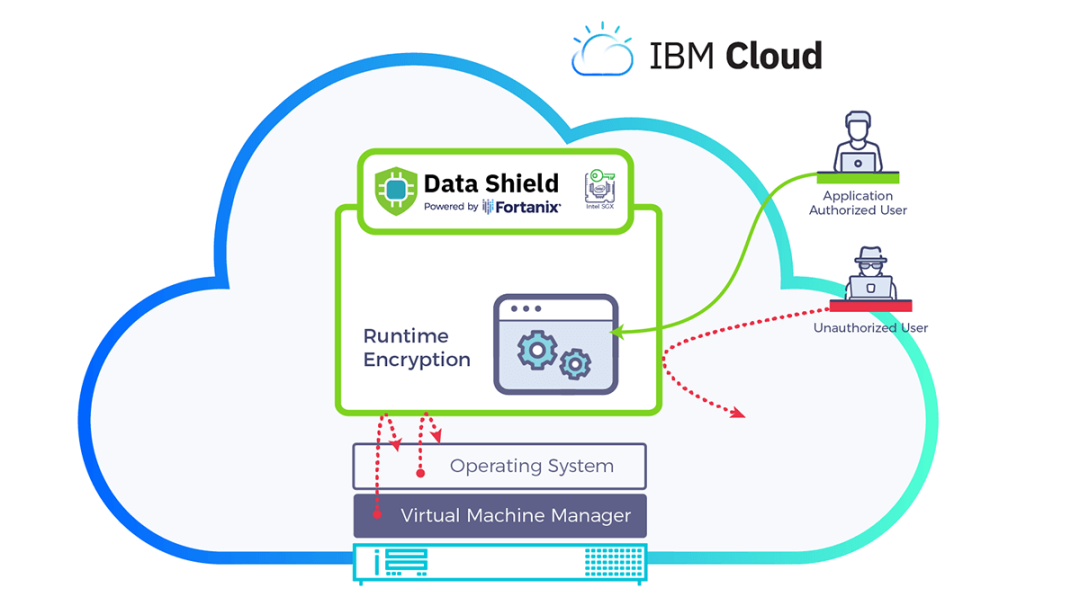
At our company, we offer a range of services and solutions to help organizations enhance their security posture on IBM Cloud. Our team of security experts can assess your cloud environment, identify potential security risks, and recommend the right security controls to mitigate these risks effectively. With our expertise and experience in cloud security, we can help you secure your cloud infrastructure and protect your critical assets from cyber threats.
Additional Information on IBM Cloud Security
IBM Cloud Security provides a broad range of security capabilities, including identity and access management, data encryption, network security, and security monitoring. These capabilities are designed to help organizations build a secure and resilient cloud environment that can withstand cyber attacks and data breaches. By leveraging IBM Cloud Security, organizations can improve their security posture and reduce the risk of security incidents in the cloud.
Conclusion
In conclusion, IBM Cloud Security offers a comprehensive set of security solutions and services to help organizations secure their cloud environments effectively. By implementing IBM Cloud Security, organizations can enhance their security posture, protect their sensitive data, and mitigate potential cyber threats. With its advanced security features and expertise in cloud security, IBM Cloud Security is a reliable choice for organizations looking to secure their cloud infrastructure and ensure the integrity of their cloud-based assets.
FAQs
1. What are the key features of IBM Cloud Security?
IBM Cloud Security offers a range of security capabilities, including identity and access management, data encryption, network security, and security monitoring.
2. How can organizations benefit from IBM Cloud Security?
Organizations can benefit from IBM Cloud Security by enhancing their security posture, protecting their sensitive data, and mitigating potential cyber threats in the cloud.
3. What sets IBM Cloud Security apart from other cloud security solutions?
IBM Cloud Security stands out for its advanced security features, expertise in cloud security, and comprehensive set of security solutions tailored for IBM Cloud environments.
4. How can organizations get started with IBM Cloud Security?
Organizations can get started with IBM Cloud Security by reaching out to our team of security experts who can assess their security needs and recommend the right security controls for their cloud environment.
5. Why is IBM Cloud Security important for organizations operating in the cloud?
IBM Cloud Security is important for organizations operating in the cloud as it helps them secure their cloud environments, protect their critical assets, and comply with industry regulations and security best practices.