Understanding FedRAMP Moderate
When it comes to data security and compliance, FedRAMP Moderate is a term that you may have heard thrown around. But what exactly does it mean, and why is it important? In this article, we will delve into the world of FedRAMP Moderate, explaining what it is, how it works, what is known about it, and how you can ensure compliance with it.
What Does It Mean?
FedRAMP Moderate is a set of security standards established by the Federal Risk and Authorization Management Program (FedRAMP). This program was created to provide a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services used by the federal government.
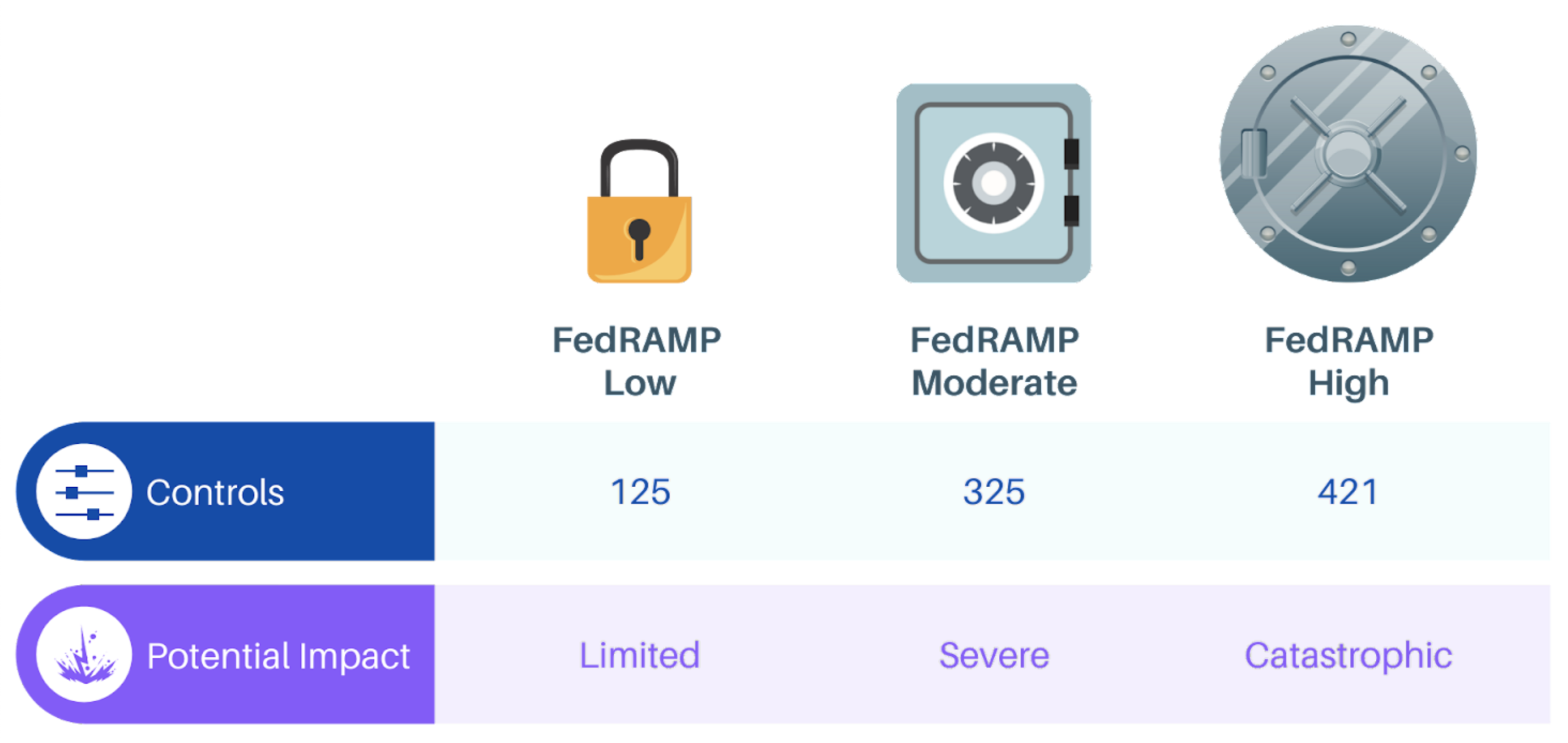
When a cloud service provider achieves FedRAMP Moderate compliance, it means that their system has been assessed and meets the security requirements set forth by FedRAMP for moderate-impact data. This includes protecting sensitive but unclassified information that, if compromised, could have a moderate adverse effect on an organization’s operations, assets, or individuals.
How Does It Work?
Cloud service providers seeking FedRAMP Moderate compliance must undergo a rigorous authorization process that includes a security assessment conducted by an accredited third-party assessment organization (3PAO). This assessment evaluates the provider’s security controls and determines if they meet the FedRAMP Moderate baseline requirements.
Once a provider has successfully completed the security assessment, they can submit their authorization package to the FedRAMP Program Management Office (PMO) for review and approval. If the package meets all of the necessary requirements, the provider will receive a FedRAMP Moderate Authorization to Operate (ATO), allowing them to offer their services to federal agencies.
What Is Known About FedRAMP Moderate?
One of the key aspects of FedRAMP Moderate is its focus on data security and risk management. Cloud service providers must implement a wide range of security controls to protect moderate-impact data, including access control, encryption, auditing, and incident response. These controls are designed to mitigate risks and prevent unauthorized access or data breaches.
Additionally, FedRAMP Moderate requires continuous monitoring of security controls to ensure ongoing compliance with the program’s requirements. Providers must regularly assess their systems, monitor for security incidents, and report any vulnerabilities or breaches to the FedRAMP PMO.
Solution for Achieving FedRAMP Moderate Compliance
For organizations seeking to achieve FedRAMP Moderate compliance, there are several steps they can take to ensure that their systems meet the necessary security requirements. This includes implementing the appropriate security controls, conducting regular security assessments, and maintaining documentation of their security posture.
Working with a qualified third-party assessment organization (3PAO) can also help organizations navigate the authorization process and ensure that they are meeting all of the FedRAMP Moderate requirements. These organizations have the expertise and experience necessary to evaluate security controls and provide guidance on how to improve security posture.
Conclusion
In conclusion, FedRAMP Moderate is a critical security standard for cloud service providers seeking to offer their services to federal agencies. By achieving FedRAMP Moderate compliance, providers can demonstrate their commitment to data security and risk management, ensuring that sensitive information is protected from unauthorized access or breaches.
FAQs
1. What is the difference between FedRAMP Moderate and FedRAMP High?
FedRAMP High is a higher level of security compliance designed for systems that handle sensitive or classified information with a high impact on an organization. FedRAMP Moderate is for systems that handle moderate-impact data.
2. How long does it take to achieve FedRAMP Moderate compliance?
The time it takes to achieve FedRAMP Moderate compliance can vary depending on the complexity of the system and the readiness of the organization. On average, the process can take several months to a year or more.
3. Can FedRAMP Moderate compliance be revoked?
Yes, FedRAMP Moderate compliance can be revoked if a provider fails to maintain the necessary security controls or comply with the program’s requirements. Providers must undergo regular security assessments to ensure ongoing compliance.
4. Are there any benefits to achieving FedRAMP Moderate compliance?
Absolutely! Achieving FedRAMP Moderate compliance can open up new opportunities for cloud service providers to work with federal agencies and demonstrate their commitment to data security and risk management.
5. How can organizations stay up to date on changes to the FedRAMP Moderate requirements?
Organizations can stay informed about changes to the FedRAMP Moderate requirements by regularly checking the FedRAMP website for updates and subscribing to their mailing list for notifications about new guidance or policy changes.
Understanding FedRAMP Moderate and how to achieve compliance with this critical security standard for cloud service providers. Learn about the requirements, process, and benefits of FedRAMP Moderate.
FedRAMP Moderate, security compliance, cloud service providers, data security, risk management, FedRAMP High, security controls