Understanding Cloud Security Threats
When it comes to the security of our data in the cloud, there are a number of threats that we need to be aware of. Cloud security threats are risks that can compromise the confidentiality, integrity, and availability of our data stored in the cloud. These threats can come in many forms, ranging from malicious attacks by hackers to accidental data breaches by employees.
So, what exactly do we mean by cloud security threats? Simply put, these are vulnerabilities in the cloud computing environment that can be exploited by cybercriminals to gain unauthorized access to sensitive information. This can include personal data, financial information, intellectual property, and more.
Cloud security threats can manifest in various ways, such as data breaches, ransomware attacks, DDoS attacks, insider threats, and more. These threats can have serious consequences for organizations, including financial losses, reputational damage, and legal repercussions. Therefore, it is crucial for businesses to take proactive measures to protect their data in the cloud.
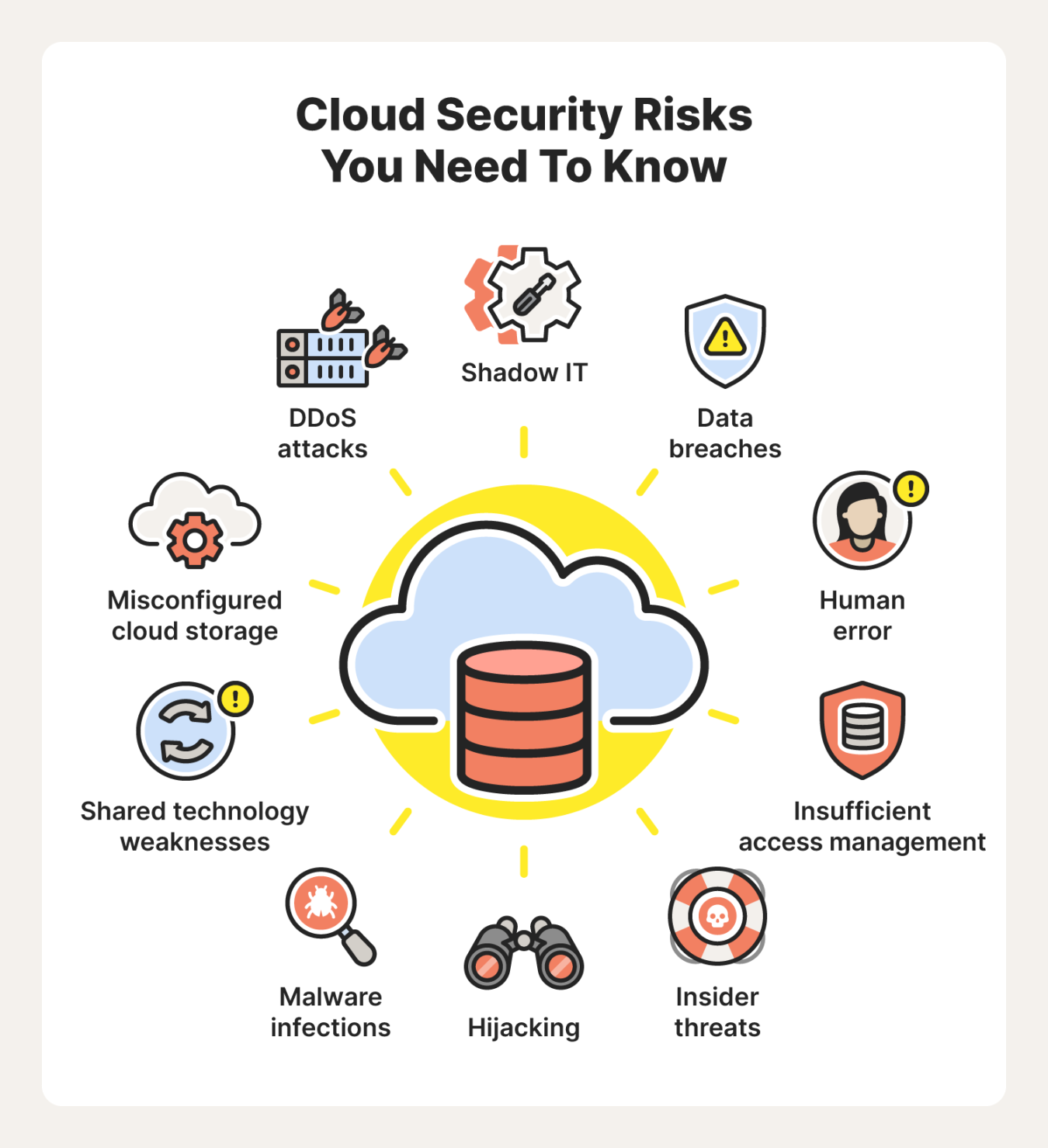
One of the most common cloud security threats is data breaches. In a data breach, cybercriminals gain unauthorized access to sensitive information stored in the cloud, such as customer data, employee records, or intellectual property. This can lead to identity theft, financial fraud, and other forms of cybercrime.
Another common cloud security threat is ransomware attacks. In a ransomware attack, cybercriminals encrypt the victim’s data and demand a ransom in exchange for the decryption key. This can result in data loss, financial losses, and business disruption. Ransomware attacks are becoming increasingly common in the cloud computing environment, so organizations need to be vigilant and prepared to defend against them.
DDoS attacks are another serious cloud security threat. In a DDoS (Distributed Denial of Service) attack, cybercriminals flood a website or online service with a large volume of traffic, causing it to become slow or unavailable. This can disrupt business operations, cause financial losses, and damage the organization’s reputation. DDoS attacks are a major concern for businesses that rely on the cloud for their operations.
Insider threats are also a significant cloud security threat. Insider threats occur when employees, contractors, or other trusted individuals intentionally or unintentionally compromise the security of an organization’s data stored in the cloud. This can include sharing sensitive information with unauthorized parties, downloading malware onto company devices, or exploiting vulnerabilities in the cloud environment.
There are many other cloud security threats that organizations need to be aware of, such as phishing attacks, malware infections, insecure APIs, and more. Each of these threats poses a unique risk to the security of data stored in the cloud, and organizations need to take a holistic approach to cybersecurity to protect against them.
So, what can organizations do to defend against cloud security threats? The first step is to conduct a thorough risk assessment to identify potential vulnerabilities in the cloud computing environment. This can include evaluating the security of cloud service providers, implementing strong access controls, encrypting sensitive data, and monitoring for suspicious activity.
It is also important for organizations to educate their employees about the risks of cloud security threats and provide training on best practices for data security. This can help employees recognize and respond to potential threats, such as phishing emails, suspicious links, or unauthorized access attempts.
Furthermore, organizations should regularly update their security measures to address new and emerging cloud security threats. This can include installing security patches, updating antivirus software, and implementing multi-factor authentication. By staying proactive and vigilant, organizations can reduce the risk of falling victim to cloud security threats.
In conclusion, cloud security threats are a serious concern for organizations that store data in the cloud. These threats can manifest in various forms, such as data breaches, ransomware attacks, DDoS attacks, insider threats, and more. By taking proactive measures to protect their data, organizations can mitigate the risk of falling victim to these threats and safeguard their sensitive information.
FAQs
1. What are some common cloud security threats?
Common cloud security threats include data breaches, ransomware attacks, DDoS attacks, insider threats, phishing attacks, malware infections, and insecure APIs.
2. How can organizations defend against cloud security threats?
Organizations can defend against cloud security threats by conducting risk assessments, implementing strong access controls, encrypting sensitive data, educating employees about data security best practices, and regularly updating security measures.
3. What are the consequences of falling victim to cloud security threats?
The consequences of falling victim to cloud security threats can include financial losses, reputational damage, legal repercussions, data loss, business disruption, and more.
4. Why are insider threats a significant cloud security concern?
Insider threats are a significant cloud security concern because employees, contractors, or other trusted individuals can intentionally or unintentionally compromise the security of an organization’s data stored in the cloud.
5. How can organizations stay proactive and vigilant against cloud security threats?
Organizations can stay proactive and vigilant against cloud security threats by regularly updating security measures, conducting employee training on data security best practices, and monitoring for suspicious activity in the cloud computing environment.